Now that we have an intuitive sense of how Bitcoin needs to address the problem of trust between network participants, we can get a bit more specific. The blockchain is collaboratively maintained by anonymous peers or nodes on the network and Bitcoin requires that each node prove a significant amount of work was invested in the creation of a block of transactions. This is to ensure that untrustworthy peers who want to modify past blocks have to work harder than honest peers who only want to add new blocks to the blockchain. And because the blocks are chained together, the cost to modify a particular block increases with every new block added to the blockchain. This is because work will have to be done in order to reconstitute subsequent, linked blocks over and above just the block being tampered with, at a faster rate than what other blocks are being added to the valid blockchain. The chaining magnifies the effect of the proof of work.
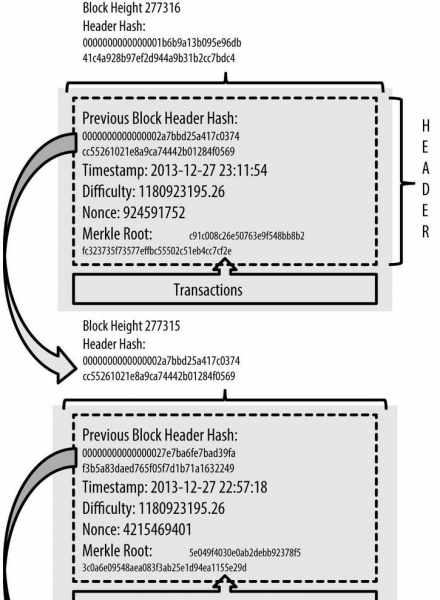
Recall the previous agreement between the Byzantine generals that the message modification (through the addition of a nonce variable) needs to yield a particular type of hash? Well more specifically, the requirement for Bitcoin is that a nonce needs to be found (mined) such that SHA-256(SHA-256 (header contents + nonce)) is less than a certain target value. And furthermore, the difficulty of mining this nonce can be adjusted by adjusting this difficulty target. The block structure is conceptually represented in the diagram to the right:
Block generation difficulty
Both the nonce and the difficulty target is included in the block header. The target is the threshold below which a block header hash too, must be in order for the block to be considered valid by the network. It is stored in an nBits encoded form in the header. The SHA-256(SHA-256()) hash output of a block’s header must be lower than or equal to the current target for the block to be accepted by the network.
The lower the target, the more difficult it is to generate a valid block. This is because of the seemingly random nature of cryptographic hashes. The larger the target is, the more likely your random hash output is likely to fall below the target.
It’s important to realize that block generation is similar to a lottery. Each hash output is a random number between 0 and the maximum value of a 256-bit number (which is huge). If your hash is below the target, then you win. If not, you increment the nonce and try again.
Adjusting the difficulty target to maintain block generation time
A valid block is produced, on average, every ten minutes.
Every 2,016 blocks, the network uses timestamps stored in each block header to calculate the number of seconds elapsed between the generation of the first and last of those last 2016 blocks. The ideal value is 1,209,600 seconds (two weeks, or 10 minutes per block). If it took fewer than two weeks to generate the 2016 blocks, it implies that there is more computing or hash power on the network producing hashes and valid blocks at a faster rate. The expected difficulty value would then be increased proportionally so that the next 2016 blocks should take exactly two weeks to generate if hashes are checked at the same rate.
If it took more than two weeks to generate the blocks, it implies that there is less hash power on the network. This could, for example, be the result of miners switching off mining computers in order to reduce their operating costs. The expected difficulty value would then be decreased proportionally for the same reason.
Chaining the blocks together
Because each block header must hash to a value below the target threshold, and because each block is linked to the block that preceded it, it requires (on average) as much hashing power to build a chain on top of a modified block as the entire Bitcoin network expended between the time the original block was created and the present time. Only if you acquired a majority of the network’s hashing power could you reliably execute such a 51 percent attack against the network. Although, having less than 50% of the network’s hashing power still gives one reasonable chance of performing such attacks.
Any Bitcoin miner who successfully hashes a block header to a value below the target threshold can add the entire block to the blockchain (assuming the block is otherwise valid). These blocks are commonly addressed by their block height—the number of blocks between them and the first Bitcoin block (block 0, most commonly known as the genesis block). For example, block 2016 is where difficulty could have first been adjusted.
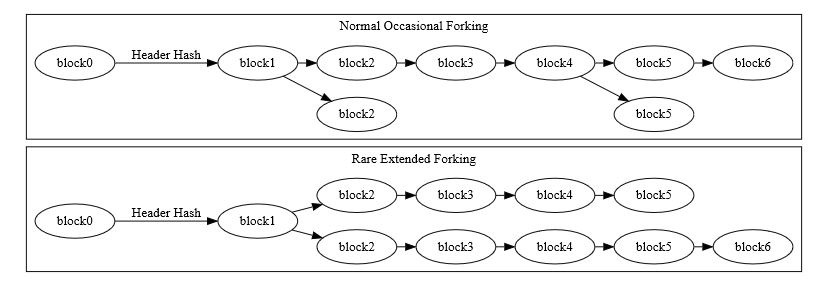
Multiple blocks can all have the same block height, as is common when two or more miners each produce a block at roughly the same time. This creates an apparent fork in the chain, as shown in the illustration below:
Having less than 50% of the network’s hashing power still gives one reasonable chance of performing 51% attacks against the network.
When miners simultaneously produce blocks at the end of the blockchain, each node individually chooses which block to accept. In the absence of other considerations, nodes usually use the first block they see, but continue to monitor subsequent blocks being mined, building two chains in the process. Eventually a miner produces another block which attaches to only one of the competing simultaneously-mined blocks. This makes that side of the fork stronger than the other side. This is where the magic comes in, and why it is so difficult for a bad actor to attack the Bitcoin network.
The power of Proof of Work – fending off a network attack
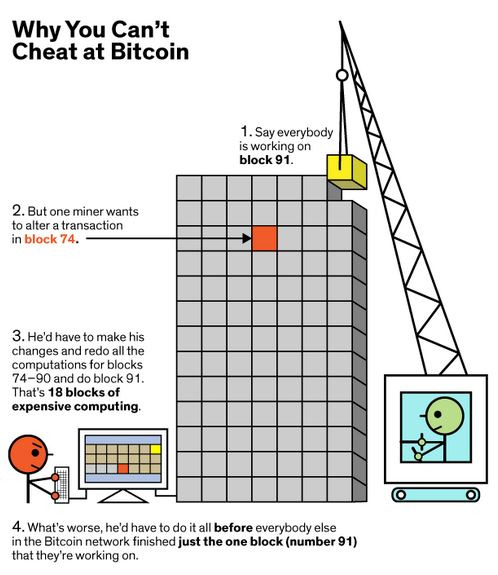
Because creating a winning block is more likely with massive computational power, a fraudulent node will have to have an inordinate amount of computational power to continuously create more winning blocks to extend the chain on top of its fraudulent block. It becomes virtually impossible to continuously beat other miners and extend its chain by even 3, 4 or 5 blocks. This forked, dishonest chain will then be discarded as the network only adds blocks that required the most cumulative computational power to be created. The diagram to the right is a simplistic but very intuitive analogy to convey this concept.
Assuming a fork only contains valid blocks, normal peers always follow the most difficult chain to recreate and throw away stale blocks belonging to shorter forks. Stale blocks are also sometimes called orphans or orphan blocks. Long-term forks are possible if different miners work at cross-purposes, such as some miners diligently working to extend the blockchain at the same time that other miners are attempting a 51 percent attack to revise transaction history.